
Compromised passwords are a major cybersecurity issue regardless of the size of your business. In 2019, 80% of data breaches were due to stolen or hacked login credentials.
Passwords cause IT security problems for two main reasons:
- Users use poor password habits that allow passwords to be hacked.
- Cybercriminals often hack large databases of usernames and passwords at major organizations (Facebook, Marriott, U.S. Cellular, etc.)
Even with strong password habits, such as the use of unique passwords that are a combination of numbers, letters and symbols, companies can still find that their corporate accounts are being compromised. All it takes is a breach of a site that one of your employees has an account with to put you at risk of a breach.
And those large-scale data breaches are all too common these days. The State of Connecticut recently received a $17.5 million settlement, along with 45 other states, from Home Depot over a breach that exposed the personal details of approximately 40 million customers.
While you may not have quite that many customer records in your business, it is just as important for you to keep your company data secure and protected from a breach of one of your accounts.
Two-Factor Authentication (2FA) is 99.9% Effective
One of the best ways to safeguard your online accounts is through the use of 2FA. According to Microsoft, which gets hit with 300 million fake sign-in attempts each day to their cloud services, enabling 2FA stops 99.9% of those account attacks.
Enabling 2FA is no longer just a “good idea”. It is vital to your company’s cybersecurity due to the rise in password theft and account compromise. In order for two-factor authentication to be effective, it should be implemented with a strategy. If you just begin turning on 2FA for all of your accounts, you can run into issues with user pushback and security consistency.
Consider These Factors Before Implementing Two-Factor Authentication
How Many Accounts Need 2FA?
The average small and mid-sized business (SMB) employee uses about 8 different SaaS tools. That is eight different accounts that they need to log into. This is in addition to any other logins they have for remote connections or other internal systems.
Additionally, each small business has between 40-79 different cloud apps that it uses. If you don’t put together a full list of every account that uses a login, you could easily forget to add some to your 2FA strategy (which will leave you vulnerable).
Besides reviewing app use with your managers, it is important to survey employees. Often employees will use apps on their own (especially if they’re remote) without their company realizing it. It is vital to know of these apps (called “shadow IT”) so that you can have every account protected.
Consider Using a Single Sign-On (SSO) Technology
We have just gone over the fact that employees use multiple cloud apps in their daily workflow. If you enable two-factor authentication separately in the app for each one, that could be 8 different app experiences that staff have to go through several times per day to access their work.
Not using an integrated approach to 2FA, like SSO, leads to employee backlash because of the inconvenience of stopping to put in the 2FA code several times per day for each app.
63% of surveyed businesses say they have received employee backlash when trying to implement two-factor authentication.
An SSO application allows you to integrate all of your logins into a single experience. Employees log in once, enter the 2FA once and can access all of their tools. This streamlines the experience, improves productivity and reduces backlash to 2FA.
Which Way Should the 2FA Code Be Received?
There are three main methods for implementing 2FA. Each one delivers the 2FA code a little differently. Not all methods have the same level of security or the same level of convenience for the user.
As you can probably guess, the most convenient method is the least secure and the least convenient method is the most secure.
However, even with the difference in security levels, the effectiveness of 2FA (as tested with three different methods of attack) was found in a Google study to be between 76% to 100% effective.
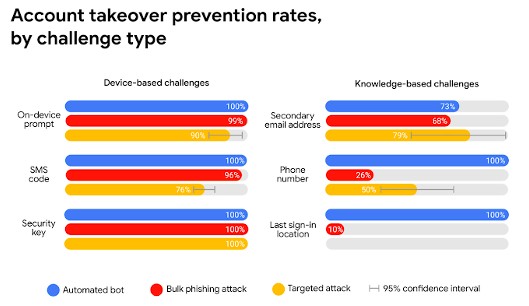
Google Study for Two-Factor Authentication Methods
The three methods to choose from for receiving the 2FA code are:
- Security Key: This is a separate device (about the size of a USB drive) that is inserted into a mobile device or computer to authenticate the code. This is the most secure method as well as the most expensive method. It’s also a little less convenient due to the need to carry around a separate device.
- On-Device Prompt: Using an on-device prompt through an authentication app has the middle-range of balance between security and convenience.
- SMS/Text: Receiving the 2FA code by text message is the most convenient method and most familiar to users. However, it is the least secure due to the ability for SIM cards to be cloned using malware.
Implement 2FA & Keep Your Users Secure & Productive
Sound Computers can help your Connecticut business with the fluid implementation of two-factor authentication that doesn’t inconvenience users and keeps your accounts secure.
Contact us today to schedule a free consultation. Call 860-577-8060 or reach us online.
