
Cloud computing has revolutionized the way businesses operate. It offers scalability, flexibility and cost-efficiency. However, cloud services also come with a downside: cloud waste.
Cloud waste is the unnecessary spending of resources and money on cloud services. These services are often not fully utilized or optimized. About 32% of cloud spending is wasted. This can lead to budget concerns as spending skyrockets.
That figure also holds opportunity. It means that you can reduce nearly a third of cloud spending by optimizing how you use cloud tools.
How can you reduce cloud waste at your business and save money? Here are some smart tactics to consider.
Conduct a Comprehensive Cloud Audit
Before implementing any cost-cutting strategies, conduct an audit. It is essential to have a clear understanding of your current cloud usage. Conducting a comprehensive cloud audit allows you to identify:
- Underutilized resources
- Overprovisioned instances
- Unnecessary services
Use cloud management tools to generate reports. Look at usage patterns, costs and performance metrics. This initial assessment forms the foundation for implementing effective waste reduction tactics.
Put in Place Right-Sizing Strategies
Right-sizing involves matching your cloud resources to the actual demands of your workloads. Many businesses fall into the trap of overprovisioning. This means securing more user licenses or features than they need. This leads to increased costs and unnecessary waste.
Analyze your workload requirements and resize instances accordingly. Use tools provided by your cloud service provider. These tools can identify and adjust the capacity of instances. This ensures that you only pay for the resources you truly need.
Use Reserved Instances and Savings Plans
Cloud providers offer cost-saving options like Reserved Instances (RIs) and Savings Plans. These allow businesses to commit to a specific amount of usage. This is in exchange for discounted rates. By leveraging these options, you can significantly reduce your cloud costs over time.
Carefully analyze your workload and usage patterns. Then determine the most cost-effective reserved capacity or savings plan. Find a plan that aligns with your business' long-term goals.
Install Automated Scaling Policies
Dynamic workloads have a need for dynamic resource allocation. Install automated scaling policies. These ensure that your infrastructure scales up or down based on demand. This optimizes performance. It also prevents overprovisioning during periods of low activity.
Cloud services enable you to set predefined policies for scaling. Examples are AWS Auto Scaling and Autoscale in Azure. These features help ensure efficient resource utilization without manual intervention.
Track and Optimize Storage
Storage costs can accumulate quickly. This is especially true when data is not regularly reviewed and archived. Estimate your storage needs. Put in place lifecycle policies to automatically downsize lesser-used data such as transitioning less frequently accessed data to lower-cost storage options.
Regularly review and delete unnecessary data to free up storage space. Adopt a proactive approach to storage management. This can help you significantly reduce costs associated with data storage.
Schedule Your Cloud Resources
Schedule your cloud resources to run only when you need them. For example, turn off development, testing or staging environments during nights and weekends or scale down your production environment during off-peak hours.
Use available tools to automate the scheduling of your cloud resources. Base this on automated rules and policies that you define.
Delete Unused or Orphaned Cloud Resources
Sometimes you may forget or neglect to delete cloud resources that you no longer need or use. This can include:
- Snapshots
- Backups
- Volumes
- Load balancers
- IP addresses
- Unused accounts
These resources can accumulate over time and incur unnecessary costs. To avoid this, you should regularly audit your cloud environment. Delete any unused or orphaned resources that your business is not using. You can often use cloud provider tools to find and remove these.
Weed Out Duplicate Services
Different departments in the same organization may be using duplicate services. Marketing may use one task management app while Sales uses a different one. Centralize cloud resources and remove duplicate tools.
Having everyone use the same cloud tool for the same function can save money as well as enhance collaboration, reporting and data integration.
Embrace Serverless Architecture
Serverless computing allows businesses to run applications without managing the underlying infrastructure. You pay only for the actual compute resources used for your processes. This eliminates the need for provisioning and maintaining servers which reduces both operational complexity and costs. Consider migrating suitable workloads to a serverless model. This can help you optimize resource use and cut cloud waste.
Schedule a Cloud Optimization Assessment Today
By following these smart tactics, you can reduce cloud waste at your business as well as optimize your cloud spending. This helps you save money. You can also improve operational efficiency and environmental sustainability.
Are you struggling with expanding cloud costs? Need help identifying and removing cloud waste? Our team of cloud experts can help you.
Contact us today to schedule your assessment.

In an age where businesses increasingly rely on cloud computing for their operations, the issue of cloud waste has become a significant concern. Cloud waste refers to the unnecessary or inefficient use of cloud resources which lead to inflated costs and decreased efficiency. Read more

The global pandemic put a big emphasis on the need to run a business from anywhere. Enabling employees to work remotely requires cloud solutions. This includes collaborative platforms like Google Workspace and Microsoft 365. VoIP (Voice over Internet Protocol) phone systems have also become critical.
VoIP allows companies to stay in contact with customers and potential customers. Employees can work from anywhere and still answer the business phone line. Callers get a similar experience regardless of where employees may be working (office or home).
When you have people working from home, those old landline systems are inefficient. This has led to a large movement by businesses to VoIP because of necessity and cost-savings.
According to Microsoft, 82% of organizations have reported saving money after implementing VoIP.
While VoIP is the way to go for the future, this doesn’t mean that it is foolproof. Companies that don’t set up their system efficiently can experience issues. This includes things like dropped calls, low bandwidth and features left unused.
If you have been struggling to make your cloud phone system more efficient, check out these tips below. They provide the best setup practices for VoIP. Use these to positively impact your bottom line.
1. Check Network Capabilities
You can’t just assume that you can enable a VoIP system and all will be well. Your network may not be able to handle the extra bandwidth needs without adjustments.
Things that you want to look at include jitter and packet loss. Additionally, review router settings to make sure it can handle peak traffic times. Experiencing dropped calls or choppy audio shows a need to address issues. These may include adjusting network hardware and/or increasing your ISP bandwidth.
2. Prioritize Your VoIP Software Using QoS Rules
Quality of Service (QoS) is a router settings area that allows you to say which traffic is most important. If QoS is not in place, it means resource issues. A large cloud backup could kick in and interrupt your calls because it is taking up bandwidth.
QoS sets up “traffic lanes” that give priority to certain functions. You will want to have your VoIP software prioritized to get the bandwidth it needs. This avoids issues with less critical processes hogging up internet resources.
Using QoS keeps your calls smooth. It also improves the reliability of your cloud phone system. It is also a good idea to use these rules for other important cloud activities.
3. Provide Quality Headsets for Your Team
A cheap headset can ruin the call experience for a potential customer. If someone calls in and can’t hear anything or gets choppy reception, they will quickly get frustrated. They will most likely figure that your company doesn’t have its act together.
Your employees may not be able to afford high-quality headsets. They also may not know what type to buy. Head off potential problems by issuing quality headsets for your team to use.
4. Set Up Departments & Ring Groups
One of the great features of VoIP phone systems is the ability to set up ring groups. You first set up your department groups (accounting, marketing, etc). Then set up the included employee extensions.
Creating a ring group allows you to have a call go to your customer support department as a whole. This is better than one person who may be busy. This way the whole group gets the ring and the first available person can pick up.
Ring groups improve the caller experience by reducing the wait time. It can also mitigate the need for the caller to leave a voicemail and get stuck waiting on a call back.
5. Create Your Company Directory
Auto assistants are extremely helpful and nearly all VoIP systems have them. You set up your company directory first and then record messages to prompt the caller.
For example, you can set up a message that prompts them to input the last name of the person that they are trying to reach. If they aren’t calling a specific person, they can be routed to a department.
While setting up a company directory takes a little effort up front, it will save much more. You no longer will need to have someone specifically routing every call. Callers can also get to the person or department they need faster. This improves the customer experience and boosts office productivity.
6. Have Employees Set Up Their Voicemail & VM to Email
When you get out of a long meeting, going through a bunch of voicemails can take time. Instead of needing to listen to each one to see which calls are a priority, you could simply read through them.
The voicemail to email feature in VoIP phone systems will automatically transcribe voicemails. They are then emailed to the recipient. This improves efficiency. It also eliminates wasted time spent on listening to entire messages to know who called.
Have employees set up this feature with their extension and email address. Some VoIP systems also offer an option to have transcribed voicemails sent via SMS.
7. Train Your Team on the Call Handling Process
Don’t leave your employees to jump in and learn a VoIP system themselves. It is important to train them on the features and the company calling process. This ensures that your team can enjoy all of those time-saving features.
Get Help Enhancing Your Business Phone System
Need help improving your business phone system? Looking for a better customer experience? Give us a call and schedule a consultation. We can help!

Cloud misconfiguration has become one of the most significant threats to cloud security. Cloud vulnerabilities have increased by 28% since last year. There was an increase in the offer of cloud accounts on the dark web of 200%. The catastrophic impact of cloud misconfiguration has made it clear that proper cloud security and configuration is of the utmost importance.
Cloud breaches constantly make news headlines and the ambiguity that surrounds cloud misconfiguration can seem daunting. Many businesses have lost sensitive data and have been open to cyber-attacks and malware due to cloud misconfiguration.
According to the Business wire, cloud misconfiguration issues are responsible for 80% of data breaches.
With businesses relying on the cloud to store and secure their data, hackers have found much of their success in targeting companies due to misconfigured clouds. The question arises: Is misconfiguration leaving your cloud accounts at risk and its resources being advertised to malicious hackers?
What is cloud misconfiguration?
Cloud misconfiguration is errors, gaps or glitches in the cloud environment that could expose your business to risk. These risks come in the form of insider threats and attacks, cloud breaches, data breaches, malware, security breaches, ransomware or external hackers that could leverage the vulnerabilities available in your cloud environment to gain access to your network.
According to the National Security Agency (NSA), cloud misconfiguration is among the top vulnerabilities in the cloud environment. Cloud misconfiguration is quite complicated and can be very challenging to detect and manually remediate.
How Cloud Misconfigurations Occur
Cloud misconfigurations happen in various ways and for various reasons. Many cloud misconfigurations occur due to human errors and factors such as not enough understanding of the security practices and complex infrastructure.
- Human Error
According to Gartner, until 2025, 99% of cloud issues will be due to human error. Due to the complexity of the cloud infrastructure, employees or customers frequently grant many unrestricted accesses and fill in personal information on any website they open. When many businesses attempt to use tools from cloud vendors to manage identity and access, there may still be gaps.
- Not Enough Understanding of the Security Practices
When creating and managing apps and infrastructure, the majority of developers and DevOps teams do not place a high priority on security. These teams primarily concentrate on ensuring that the cloud environment and services work properly and offer effective functionality to users.
- Complex Infrastructure
When the cloud environment becomes complex, mistakes are bound to happen that open up a way for cyber-attacks to occur. These errors can occur due to adding or creating new containers, creating resources and altering the configurations.
Without some kind of uniformity within your cloud environment, it can be challenging to navigate and use.
What Can Happen When Cloud Misconfiguration Occurs?
Here are some things that happen when cloud misconfiguration occurs:
- Causes Data Breaches
Many businesses are unaware of the number of users in their cloud environment with excessive access to permissions. As a result of this, they are unable to know if there is a problem until after an attack. This can result in severe data loss.
- Opens a Channel for Cyber Criminals to Exploit
Once cloud misconfigurations occur, your environment is open to various vulnerabilities which opens a channel for cyber criminals to exploit and makes it easy for them to access cloud-stored data, steal it, ransom it, install malware and sometimes sell it on the dark web.
- Install Digital Skimming Code
Digital skimming attacks include inserting malicious code into a website's scripts which are loaded when a user attempts to access the site in their browser. This code intercepts sensitive information entered by the users such as account numbers, social security numbers, credit card details, etc. This information is then sent to a server controlled by the hacker. This information is then gathered, sold and otherwise illegally exploited.
- Exposing Sensitive Data
Cloud misconfigurations can lead to the exposure of confidential and sensitive data or put important files at risk of theft. Cloud misconfiguration gives hackers access to your database or cloud storage, puts your business at risk of corporate espionage and exposure of user data and makes it possible for them to erase crucial data.
- Services Disruption
Once hackers gain access to your servers or network, they have the ability to disrupt your service. This disruption can include malware, insider or ransomware attacks.
How to Protect your Cloud and Prevent Cloud Misconfiguration
The good news is that if misconfiguration is leaving your cloud accounts at risk, you can implement several best practices to protect your cloud-based assets better and prevent a misconfiguration attack.
- Implement Log-Tracking Practices
Enabling logging to control the number of users making changes in your cloud environment can protect your cloud. By tracking changes made, you will be able to identify the root cause of any misconfiguration incidents.
- Enable Encryption
Enabling encryption using cloud computing services keeps your data safe from unauthorized viewing.
- Check Permissions
Reduce permissions to only people who need access to carry out their jobs. Widespread access weakens your business security.
- Perform Regular Misconfiguration Audits
Performing regular audits ensures your cloud environment is always secure. This helps to look for signs of misconfigurations and other cloud threats.
- Practice Strong Security Policies
Set up strong security policies for all cloud infrastructure processes. Also, your employees should be informed about the policies so they don't misconfigure the cloud setting without knowing.
- Standardize Your Environments
Instead of having a complex cloud infrastructure for every deployed component, standardize some components and deploy them using templates. Once they are standardized, team members can quickly see various component configurations and boost environment management.
- Document Everything
Ensure your environment configurations and documentation are documented and backed up. This lets you compare the new environment with the intended one and also play an essential role in helping your business track what goes wrong, troubleshoot and figure out what to do.
Secure Your Cloud Environment from Misconfigurations
Sound Computers can help your Connecticut business stay protected from cloud misconfigurations while boosting your business productivity.
Contact us today to schedule a free consultation. Call 860-577-8060 or reach us online.
Cloud file storage revolutionized the way we handle documents. Gone were the days of needing to email files back and forth. No more wondering which person in the office has the most recent copy of a document.
Between 2015 and 2022, the percentage of worldwide corporate data stored in the cloud doubled. It went from 30% to 60%. A majority of organizations use cloud storage of some type. Typical services include OneDrive, Google Drive, Dropbox and others.
However, cloud storage can get messy just like the storage on your computer’s hard drive. Files get saved in the wrong place and duplicate folders get created. When employees are sharing the same cloud space, it's hard to keep things organized. Storage can be difficult to keep efficient.
Disorganized cloud storage systems lead to problems. This includes having a hard time finding files as well as spending a lot of extra time finding needed documents. It is estimated that 50% of office workers spend more time looking for files than they do actually working.
Has your office been suffering from messy cloud storage? Does it seem to get harder and harder to find what you need? Review the tips below. They include several ways to tidy up shared cloud storage spaces and save time.
Use a Universal Folder Naming Structure
One person in an office might choose to name a folder by client name. Another person might use the type of industry. When people use different naming structures for folders, it’s harder for everyone. They often can't find what they need. It also leads to the creation of duplicate folders for the same thing.
Use a universal folder naming structure that everyone follows. Map out the hierarchy of folders and how to name each thing. For example, you might have “departments” as an outer folder and nest “projects” inside.
With everyone using the same naming system, it will be easier for everyone to find things. You also reduce the risk of having duplicate folders.
Keep File Structure to 2-3 Folders Deep
When you have too many folders nested, it can take forever to find a file. You feel like you must click down one rabbit hole after another. When people need to click into several folders, it discourages them from saving a file in the right place.
To avoid this issue, keep your file structure only two to three folders deep. This makes files easier to find and keeps your cloud storage more usable.
Don’t Create Folders for Fewer Than 10 Files
The more folders people have to click into to find a document means the more time it takes. Folders can quickly add up as employees create them because they don't know where a file should go.
Use a rule for your cloud storage that restricts folder creation to 10 files or more. This avoids having tons of folders with less than a handful of files in them. Designate someone that can act as a storage administrator. This can then be the person someone asks if they’re not sure where to store a file.
Promote the Slogan “Take Time to Save It Right”
File storage can get disorganized fast when people save files to a general folder. We are all guilty from time to time of saving to something general (like the desktop on a PC). We tell ourselves that we will go back at some point and move the file to where it should be.
This issue multiplies when you have many people sharing the same cloud storage space. Files that aren’t where they belong add up fast. This makes it harder for everyone to find things.
Promote the slogan “take time to save it right” among the staff. This means that they should take the extra few seconds to navigate where the file should be and save it. This keeps things from getting unmanageable. If you use a file structure that is only 2-3 folders deep, this should be easier for everyone to abide by.
Use Folder Tags or Colors for Easier Recognition
Many cloud file systems allow you to use color tagging on folders. Using this can make a folder or group of folders instantly recognizable. This reduces the time it takes to find and store files.
For example, you could color all folders dealing with sales as green. Folders for marketing could be orange. The brain can make the connection to a topic faster when you look at a color than when reading through text.
Declutter & Archive Regularly
Files get created at a dizzying pace these days. The more files you add to a cloud storage system means the harder it is to sort through to find what you need. This is true even if the file storage is well organized.
Keep older files from making it harder to find new ones. Do this by decluttering and archiving on a regular basis. This involves having an admin delete any unnecessary files once per month. For example, delete duplicate files or old draft versions of a document.
You should also have an archiving system in place that puts all older files in one big archive folder. This keeps files that aren’t actively used any longer out of the main file path.
Come to Us for Efficient Cloud Solutions
Is your cloud storage doing what you need it to do? Do you have a disconnection between cloud storage and your other apps? We can help. Reach out to us at (860) 577-8060 or use our contact form.

Stolen login credentials are a hot commodity on the Dark Web. There are prices every type of online account from banking to social media. For example, hacked social media accounts will go for between $30 to $80 each.
The rise in reliance on cloud services has caused a big increase in breached cloud accounts. Compromised login credentials are now the #1 cause of data breaches globally according to IBM Security’s latest Cost of a Data Breach Report.
Having either a personal or business online account compromised can be very costly. It can lead to a ransomware infection, compliance breach, identity theft and more.
To make matters more challenging, users are still adopting bad password habits that make it all too easy for criminals. For example:
- 34% of people admit to sharing passwords with colleagues
- 44% of people reuse passwords across work and personal accounts
- 49% of people store passwords in unprotected plain text documents
Cloud accounts are more at risk of a breach than ever. However, there are several things you can do to reduce the chance of having your online accounts compromised.
USE MULTI-FACTOR AUTHENTICATION (MFA)
Multi-factor authentication (MFA) is the best method there is to protect cloud accounts. It is not a failsafe but it is proven to prevent approximately 99.9% of fraudulent sign-in attempts according to a study cited by Microsoft.
When you add the second requirement to a login, which is generally to input a code that is sent to your phone, you significantly increase account security. In most cases, a hacker is not going to have access to your phone or another device that receives the MFA code and thus they won’t be able to get past this step.
The brief inconvenience of using that additional step when you log into your accounts is more than worth it for the bump in security.
USE A PASSWORD MANAGER FOR SECURE STORAGE
One way that criminals get their hands on user passwords easily is when users store them in unsecured ways. This includes an unprotected Word or Excel document or the contact application on their PC or phone.
Using a password manager provides you with a convenient place to store all your passwords and is also encrypted and secured. You only need to remember one strong master password to access all the others.
Password managers can also autofill all your passwords in many different types of browsers which makes it a convenient way to access your passwords securely across devices.
REVIEW/ADJUST PRIVACY & SECURITY SETTINGS
Have you taken time to look at the security settings in your cloud tools? One of the common causes of cloud account breaches is misconfiguration. This is when security settings are not properly set to protect an account.
You don’t want to just leave SaaS security settings at defaults because these may not be protective enough. Review and adjust cloud application security settings to ensure that your account is properly safeguarded.
USE LEAKED PASSWORD ALERTS IN YOUR BROWSER
You can have impeccable password security on your end and still have your passwords compromised. This can happen when a retailer or cloud service that you use has their master database of usernames and passwords exposed and the data stolen.
When this happens, those leaked passwords can quickly end up for sale on the Dark Web without you even knowing it.
Due to this being such a prevalent problem, browsers like Chrome and Edge have had leaked password alert capabilities added. Any passwords that you save in the browser will be monitored and you will see an alert when you use it if it is found to be leaked.
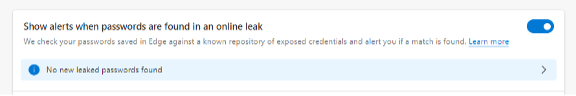
Look for this in the password area of your browser because you may need to enable it. This can help you know as soon as possible about a leaked password so that you can change it.
DON’T ENTER PASSWORDS WHEN ON A PUBLIC WI-FI
Whenever you’re on public Wi-Fi, you should assume that your traffic is being monitored. Hackers like to hang out on public hot spots in airports, restaurants, coffee shops and other places so they can gather sensitive data like login passwords.
You should never enter a password, credit card number or other sensitive information when you are connected to public Wi-Fi. You should either switch off Wi-Fi and use your phone’s wireless carrier connection or use a virtual private network (VPN) app that encrypts the connection.
USE GOOD DEVICE SECURITY
If an attacker manages to breach your device using malware, they can often breach your online account without a password needed. Just think about how many apps on your devices you can open and already be logged in to.
To prevent an online account breach that happens through one of your devices, make sure you have strong device security. Best practices include:
- Antivirus/anti-malware
- Up-to-date software and OS
- Phishing protection (like email filtering and DNS filtering)
LOOKING FOR PASSWORD & ONLINE ACCOUNT SECURITY SOLUTIONS?
Don’t leave your online account at risk. We can help you review your current cloud account security and provide helpful recommendations.
Reach out to us at (860) 577-8060 or contact us at info@soundcomputers.net.
You can read more about about cloud accounts here.

Last year, the REvil cybercrime gang ruined the Independence Day Holiday for hundreds of American businesses after successfully launching a ransomware attack. The attack forced hundreds of companies to close temporarily. REvil demanded a ransom of $70 million to unlock their files. Read more

Cloud storage has really come into its own in the last few decades. Although this technology has been around since the late 1990s, it has only recently been adopted by the masses. Today 94% of companies use cloud technology and around 50% of all corporate data is stored on the cloud.Read more
It is a scary thought. The analyst firm Gartner predicts that a whopping 99% of cloud security breaches will be the customer’s fault by 2025. This means that cloud providers (like Amazon, Microsoft and Slack) are doing an excellent job at keeping their platforms secure but their clients (businesses across the globe) are failing. Read more
It is no secret that the cloud is the future of business operations. Gartner predicts that global spending on cloud services will reach over $482 billion in 2022. That is up from the $313 billion in 2020.Read more


